No item, service or system is completely safe. Everything is accompanied by a certain amount of risk. Like any other transportation system, the Hyperloop has hazards as well. Many risks and hazards are similar to those present in current modes of transportation. However, the Hyperloop is a revolutionary mode of transportation with characteristics, such as the high speed of travel, the propulsion and suspension mechanisms, and the near-vacuum sealed-off environment. These characteristics result in hazards unique to the Hyperloop system. Therefore, an extensive analysis of potential threats and dangers to the system is required to create a safe mode of transportation. A collaboration between Delft Hyperloop and Deloitte was established to investigate the risks and hazards in the Hyperloop system.
The process of identifying and analysing risks and hazards is complex and consists of two components, namely the qualitative and quantitative analysis. The qualitative study is necessary to identify and have a clear understanding of the risks, which are then further analysed in the quantitative analysis to determine the likelihood and impact. These two analyses are crucial in the overarching safety analysis of the Hyperloop system. They give an indication as to the extra safety measures and controls that need to be implemented to suppress the consequences that risks have on the system.
Crown jewel assessment
To conduct the qualitative analysis, assets of the Hyperloop system first need to be defined. Assets are components that are of value to the greater system. The Hyperloop system and its assets can be divided in various ways. During the identification process the assets were categorized as follows: mobile, fixed, cyber, systems, processes, people, services and organization. Each asset is assessed based on the impact of the asset failing, giving an indication as to its importance. Safety, environmental, reputational, operation and regulatory impact were chosen as criteria. In a semi-quantitative ranking the most important assets are identified. These are called the crown jewels of the Hyperloop, which are crucial for Hyperloop operations and have a significant impact if failure occurs. The crown jewels range from security clearances and emergency procedures, to database servers and to pod-to-pod communication.
Risk assessment
Risk is defined as the combination of the probability of an event and the magnitude of the consequences. A certain risk can be quantified by the product of the probability of the event occurring and the expected damage given that the event occurs (Fischhoff, Watson & Hope, 1984). Historical data of failures can be used to quantify the likelihood and impact. However, for a new mode of transportation such as the Hyperloop, this data is not available. As a result, a semi-quantitative approach is applied whereby each failure mode of an asset is assessed based on likelihood and impact. Likelihood gives an indication as to the occurrence probability. Impact is assessed in terms of fatalities, injuries, financial damage, operational downtime and system damage. The risks are plotted in a likelihood-impact graph, as shown in figure 1. Each number corresponds with a failure mode of the Hyperloop system. A description of the failure modes can be found in table 1 at the bottom of this article.
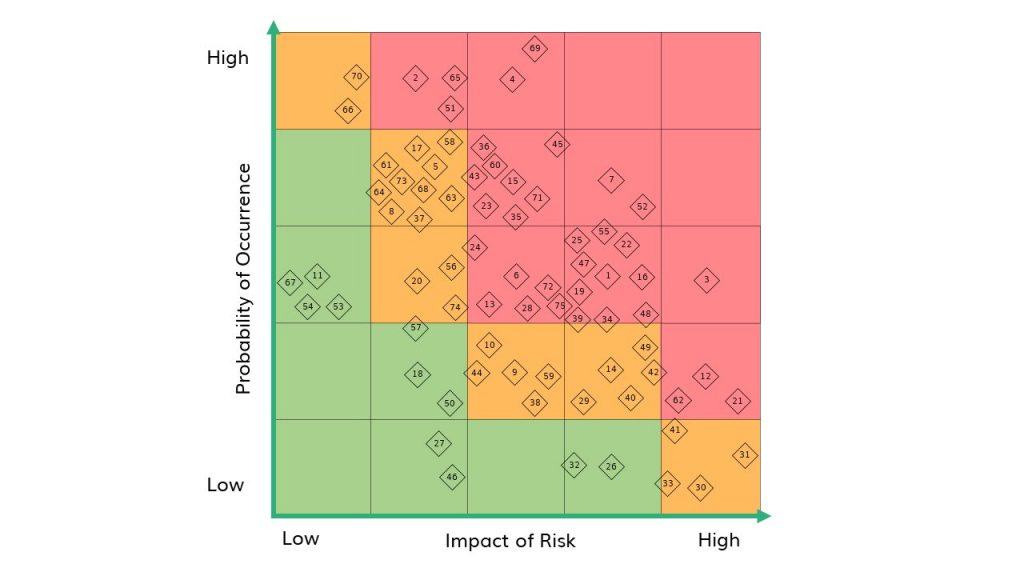
The failure modes that have a high score (the red area) pose a large risk for the system and can be found in the top right of figure 1. These risks are deemed unacceptable and have to be lowered to an acceptable level (the green area). Using the results from the semi-quantitative risk assessment, appropriate control measures can be implemented to lower the risks in the Hyperloop system. This will bring future travelers closer to a safe and reliable mode of transportation.
The goal of the collaboration between Delft Hyperloop and Deloitte was to quantify the risks of the Hyperloop. Deloitte is a company that provides its clients with a range of services, one of which being risk management. Through the collaboration between Delft Hyperloop and this branch of Deloitte, both parties were able to apply their expertise and people to share the future of mobility, thereby keeping the Netherlands moving and enable seamless travel for people and goods in a sustainable way. To be able to tackle the complex process of quantifying risks, extensive contact was maintained between Delft Hyperloop and Deloitte. Multiple meetings were held to discuss all components of the process, such as the method, assessment criteria and the scope of the investigation. After, a brainstorm session was held at Delft Hyperloop with almost 30 colleagues from Deloitte and 5 from Delft Hyperloop to identify the risks in the Hyperloop. Using these findings, the quantification of the risks was possible.
References
Fischhoff, B., Watson, S.R., & Hope, C. (1984). Defining risk. Policy sciences, 17(2), 123-139.
| Digit in figure 1 | Failure mode | Asset |
|---|---|---|
| 1 | Critical bugs (no workaround and affects critical functionality) | Software |
| 2 | Minor bugs (affects functionality, has easy workaround) | Software |
| 3 | Ransomware | Software |
| 4 | Unauthorized breach | Networks |
| 5 | Incorrect anomaly detection | Anomaly detection |
| 6 | Anomaly without detection | Anomaly detection |
| 7 | Damage to power cables | Transportation of energy |
| 8 | Broken pump | Vacuum pumps |
| 9 | Compromised component | Off-the-shelf components |
| 10 | Broken components | Off-the-shelf components |
| 11 | Sensors broken | Environmental control system |
| 12 | Loss of safe pod environment | Environmental control system |
| 13 | Data leak | Data protection |
| 14 | Backup compromise | – |
| 15 | Remote 0-day exploit | – |
| 16 | Insider threat | – |
| 17 | (Un)intentional damage to passengers | Passenger pod |
| 18 | Perishable/dangerous goods | Freight pod |
| 19 | Attack of fellow passengers | Passengers |
| 20 | Damage to pod interior | Passengers |
| 21 | Exits unable to offer protection to passengers | Emergency exits |
| 22 | Emergency exits not accessible | Emergency exits |
| 23 | Power failure | Power/communication |
| 24 | Remote attack on communications | Power/communication |
| 25 | Physical attack on power grid | Power/communication |
| 26 | Natural disaster | Power/communication |
| 27 | Electromagnetic interference | Power/communication |
| 28 | Airlock gets breached | Station/tunnels |
| 29 | People entering depressurization chamber | Station/tunnels |
| 30 | Tunnel collapses | Station/tunnels |
| 31 | Structural integrity of station fails | Station/tunnels |
| 32 | EMP attack | Battery control system |
| 33 | Solar storms | Battery control system |
| 34 | Overheating of batteries | Battery control system |
| 35 | Reduction of effectiveness of security checks | Security checks |
| 36 | Lines disrupting turn-up-and-go system | Security chekcs |
| 37 | Malfunctioning toilets | Toilets |
| 38 | Permanent magnets losing strenght | Levitation |
| 39 | Electromagnets lose power | Levitation |
| 40 | Feedback loop fails and levitation height becomes too small | Levitation |
| 41 | Hole in the tube which causes a local implosion of the tube | Vacuum environment |
| 42 | Hole in the pod which causes the loss of breathable air | Vacuum environement |
| 43 | Airlock malfunction | Vacuum environment |
| 44 | Failure of pod authorization | Communication |
| 45 | Failure of pod communication | Communication |
| 46 | Interference of external broadcasting signals | Communication |
| 47 | Failure of pod positioning | Communication |
| 48 | Braking system fails to work | Braking |
| 49 | Braking system engages at the wrong time | Braking |
| 50 | Braking system engages too fast | Braking |
| 51 | Disturbance in communication | P2P/P2I communication |
| 52 | Breach in communication system | P2P/P2I communication |
| 53 | Malfunctioning electronics | Magnetic fields |
| 54 | Damaged personal devices | Magnetic fields |
| 55 | Malfunctioning health devices | Magnetic fields |
| 56 | Wrong ticket pricing | Ticket sale |
| 57 | Data breach | Ticket sale |
| 58 | Inefficient staff | Training |
| 59 | Staff unable to act during emergency situations | Training |
| 60 | Corporate espionage | – |
| 61 | Broken sensors | System monitoring |
| 62 | Objects in tube | Maintenance |
| 63 | Incorrect maintenance | Maintenance |
| 64 | Worried passengers | Passengers |
| 65 | Incompetent employees | Employees |
| 66 | Unmotivated employees | Employees |
| 67 | Bad job fit | Employees |
| 68 | Staff not present at places where needed | Support staff |
| 69 | Invalid/incorrect maintenance | Maintenance staff |
| 70 | Too many false positives | Security staff |
| 71 | Too many false negatives | Security staff |
| 72 | Blackmailing | System integrity |
| 73 | Data sharing | System integrity |
| 74 | Malicious intent | System integrity |
| 75 | Incorrect scheduling | Scheduling |


0 Comments